Originally published at https://cyberbakery.net/ on Jan 9, 2022
In this first post this year, I am taking out my crystal ball to predict the cybersecurity outlook in 2022 and beyond. If history could indicate the future, we would not see much of a difference from 2021
Amid the impending rise of infections from the Omicron variant of COVID19 globally and closer in Australia, I would like to wish you a happy new year 2022 through this first post of the year, trusting you all had a great start to the year.
The world has changed in the past two years due to the impacts of the pandemic and the slew of sophisticated cyber-attacks. In this first post this year, I am taking out my crystal ball to predict the cybersecurity outlook in 2022 and beyond. If history could indicate the future, let me summarise some of the cybersecurity events of the last twelve months.
Top cybersecurity events and breaches of 2021
COVID and cybersecurity threats:
Coronavirus and its various variants continued disrupting our lives in 2021, and bad actors upped their game to exploit this situation. The Ireland Health Service Executive (HSE) suffered a ransomware attack during the COVID’ second wave, disrupting patient care due to the lack of access to patient information. It is estimated that HSE spent in addition to $600 million in recovery costs, including the costs of the replacement and upgrade of the systems crippled by ransomware.
JBS Foods ransomware attack and ransom:
JBS Foods, a global meat processor, experienced a Ransomware attack attributed to REvil impacting their American and Australian operations. The company might have also paid $11 million in ransom to REvil.
Log4JShell:
A new zero-day vulnerability unlike any other from the past. No one can surely say if they are not impacted. The impact of this vulnerability is wide-ranging, impacting various applications using Apache Framework’s Log4J libraries. It will take some time before we can understand the long-term impact.
Colonial Pipeline:
Colonial Pipeline, the largest fuel pipeline in the United States, suffered a data breach resulting from the DarkSide ransomware attack that hit their network in May 2021. The company, as a result, had to shut down their operations, triggering fuel shortages in the United States. During the incident, DarkSide operators also stole roughly 100GBs of files from breached Colonial Pipeline systems in about two hours.
SolarWinds:
We saw one of the most sophisticated supply chain attacks in recent times, early last year. A Russian hacking group, Cozy Bear, is attributed to the attack on the popular network management Orion platform. SolarWinds released multiple updates between March and May 2020, later identified as trojanised to install Sunburst backdoor. The SolarWind attack targeted US Government assets and a wide range of industries in the private sector.
Kaseya Supply Chain Attack:
Similar to the Solarwind Sunburst backdoor attack, another Russian hacking group REvil targeted Kaseya remote management platform to launch a ransomware attack on more than 2000 organisations globally last year.
Rise in Cybercrime:
A research organisation Cybersecurity Ventures estimates global cybercrime damage predicted to reach the US $10.5 trillion annually by 2025, up from the US $3 trillion in 2015.
Lack of Cybersecurity skills:
Cybersecurity careers have grown tremendously over the years, attributed to the increased cyber-attacks. Unfortunately, we cannot keep pace with the skills required to meet the challenge of defending applications, networks, infrastructure and people.
Increase in the amount of data needing protection:
We continue to see exponential growth in global data storage, which includes data stored in public and private infrastructure.
Hybrid work environment:
In these pandemic times, most people are working from home, which has opened up a new stream of cybersecurity challenges. This change seems to be permanent.
Predictions for 2022 & Beyond
In pandemic times, it is very difficult to predict what will happen the next day, let alone predict for the year ahead. However, let me take my crystal ball out and predict how I see cybersecurity trends for the next twelve months.
- The ransomware challenge: Bad actors are getting very creative with launching ransomware attacks. With a proven business model for the bad actors, the ransomware attacks will continue to be rampant and challenging with the new ways of delivering malicious code.
- Small and Medium Businesses (SMB): For a long time, large enterprises have been the prime focus for the bad actors. These enterprises have invested heavily to detect and respond to cyber-attack. It is getting difficult for the bad actors to launch cyberattacks against these enterprises successfully and, therefore, have shifted their focus on SMBs. SMBs often have fewer resources and, therefore, have to cut corners to prioritise cybersecurity, leaving them vulnerable to sophisticated attacks. We will see an increased number of attacks against SMBs in the year ahead.
- Passwordless: With every new application, you may have to remember another password, which often means poor password management. We know that poorly managed passwords are targets that bad actors exploit to launch attacks. In the coming year, we will see an exponential increase in the adoption of the passwordless strategy.
- Supply-Chain attack: Supply-chain attacks are going to be the norm in 2022. The bad actors will further exploit the already disrupted supply chain to extort ransom from the enterprises, threatening to exploit further their customers, similar to what we have seen in SolarWind and Kaseya attacks.
- Cyber hygiene in the hybrid work environment: Enterprises will be focusing on improving cybersecurity awareness and skills to improve the security of their home IT environment. With the security-first approach in mind, we will see a significant improvement in the overall security at home.
- Threat Hunting: More and more enterprises will increase their spending to improve or create threat hunting capabilities. Just as we see creative methods used by the hackers to exploit their victims, cyber teams have to develop capabilities to identify and stop bad actors from launching a successful cyber attack.
- AI-powered phishing attacks: The quality of phishing attacks has increased tremendously over the years. Some of these attacks are “life-like”. Bad actors are now using AI to research targets to mimic their behaviours to impersonate in the phishing campaign. Enterprises must invest in anti-fraud education in 2022 to ensure that their employees can identify good emails from bad ones.
- Software-defined (SD) world: Last few years have seen exponential growth in the software-defined world. We have seen tremendous adoption, whether a software-defined network, infrastructure, or application. 2022 will continue to see enterprises adopting SD technologies, including infrastructure as a code and serverless applications, which can be purpose-built, keeping security in mind.
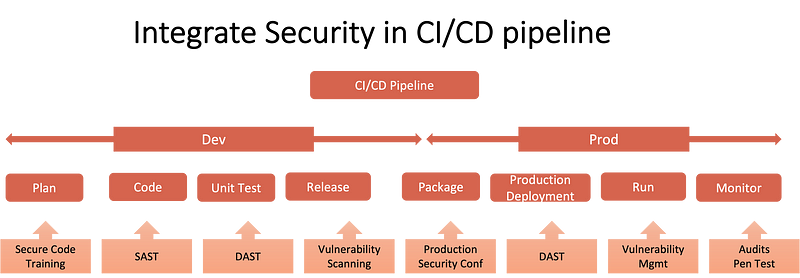
- Nation-state actors to target DevOps developers: Why would you bypass a security control if you can legitimately log in to the system? With increased adoption of the agile/DevOps methodologies, developer credentials have become the new “crown jewels” and most sort after. Hackers are targeting developers using various techniques to obtain privileged credentials. DevOps developers will continue to see being targeted this year.
2022 will continue to see nation-state threat actors exploit vulnerabilities with the ever-changing situations in regard to the dynamic geopolitical situation and similarly, scammers will be exploiting the COVID pandemic.