Your Weekly Cybersecurity Update (11 October 2024)
- Australian Government Tabled Cyber Security Bill 2024 (“Cyber Bill”)
- OpenAI Thwarts 20 Global Malicious Campaigns Utilising AI for Cybercrime and Disinformation
- Deepfakes on the Rise: Threatening Trust and Security
- Meta Ray-Ban Glasses Hacked into Real-Time Facial Recognition Tool
- Microsoft Confirms Exploited Zero-Day In Windows Management Console
- American Water Shuts Down Customer Portal Amid Cyber Security Incident
Australian Government Tabled Cyber Security Bill 2024 (“Cyber Bill”)
This week, if this legislation is passed, Australia will establish its inaugural independent Cyber Security Act, guaranteeing the presence of robust laws and safeguards within a transparent legislative structure.
The Cyber Security Legislative Package is a significant step towards aligning Australia with international best practices in cybersecurity. It includes initiatives such as mandating security standards for smart devices, reporting obligations for ransomware incidents, and establishing a Cyber Incident Review Board. The package also integrates with other legislative reforms and imposes compliance and implementation considerations for organisations. Businesses must understand and adhere to the requirements outlined in the Cyber Bill to ensure robust cybersecurity measures and avoid penalties.
The package aims to implement reforms under the Security of Critical Infrastructure Act 2018 (SOCI Act), which include clarifying existing obligations related to business critical data, enhancing government assistance measures for managing impacts of incidents on critical infrastructure, simplifying information sharing between industry and government, giving the government the power to direct entities to address risk management deficiencies, and aligning telecommunications security regulation into the SOCI Act.
OpenAI Thwarts 20 Global Malicious Campaigns Utilising AI for Cybercrime and Disinformation
OpenAI recently announced that it has disrupted over 20 deceptive operations worldwide that attempted to misuse its platform for malicious purposes. These activities included creating malware, writing articles, generating biographies for social media accounts, and producing AI-generated profile pictures for fake accounts. OpenAI stated that substantial breakthroughs have not been observed in the ability of threat actors to create new malware or build viral audiences. The company also thwarted deceptive social media content related to elections in the U.S., Rwanda, India, and the European Union and disclosed the efforts of an Israeli commercial company named STOIC in generating social media comments about Indian elections.
OpenAI highlighted specific cyber operations, such as SweetSpecter’s reconnaissance and unsuccessful spear-phishing attempts, Cyber Av3ngers’ research into programmable logic controllers, and Storm-0817’s debugging of Android malware and scraping of Instagram profiles. The company also took steps to block clusters like A2Z and Stop News, which generated content for various websites and social media accounts. Additionally, OpenAI identified Bet Bot and Corrupt Comment for using their API to engage users on a specific platform and direct them to gambling sites.
The disclosure comes after OpenAI banned accounts associated with an Iranian covert influence operation called Storm-2035, which leveraged ChatGPT to generate content focusing on the U.S. presidential election. Furthermore, cybersecurity company Sophos reported that generative AI could be exploited to spread tailored misinformation through microtargeted emails, allowing for the dissemination of political campaign websites, AI-generated personas, and email messages tailored to specific campaign points. This new level of automation enables the spread of misinformation at scale, potentially influencing people’s perceptions of political movements and candidates.
Deepfakes on the Rise: Threatening Trust and Security
Deepfakes, AI-generated forgeries of videos and audio, are surging in 2024. Experts predict a 60% increase in incidents this year, with potential damages exceeding $40 billion by 2027, primarily targeting financial institutions.
This rise in deepfakes is eroding trust in institutions and governments. Deepfakes are becoming so sophisticated that they are being used in nation-state cyberwarfare. A recent US Intelligence Community report highlights Russia’s use of deepfakes to target individuals in war zones and unstable political environments.
Deepfake Attacks on Businesses
- CEOs are a prime target for deepfake attacks. This year, a deepfake impersonating the CEO of the world’s largest advertising firm was used in a scam attempt.
- Deepfakes are also being used in financial scams. In one instance, a deepfake of a CFO and senior staff tricked a finance worker into authorizing a $25 million transfer.
Combating Deepfakes
- OpenAI’s latest model, GPT-4o, is designed to combat deepfakes. This system can identify synthetic content using techniques like Generative Adversarial Networks (GAN) detection and voice authentication.
- GPT-4o also performs multimodal cross-validation, checking for inconsistencies between audio, video, and text data.
The Importance of Trust and Security
- The rise of deepfakes underscores the critical need for trust and security in the AI era.
- Companies like Telesign are developing AI-powered solutions to combat deepfakes and digital fraud.
The Role of Skepticism
- Cybersecurity experts emphasize the importance of healthy scepticism when encountering online content. Critically evaluate information before accepting it as genuine.
The future of AI security likely involves a combination of advanced detection models like GPT-4o and a healthy dose of user scepticism.
Meta Ray-Ban Glasses Hacked into Real-Time Facial Recognition Tool
Two Harvard students have demonstrated a modified version of Meta’s Ray-Ban smart glasses that utilise AI-powered facial recognition to identify strangers in real-time.
The modified glasses use a built-in camera to capture a person’s face and search the internet for publicly available information. This information can include a person’s name, address, phone number, and details about their family members.
The students showcased the capabilities of the hacked glasses by identifying strangers on the street and then using the gathered information to strike up conversations under false pretences.
Raising Awareness of Privacy Concerns
The students have emphasized that their project is intended to raise awareness of the potential privacy risks associated with widely available consumer technology, facial recognition software, and public databases. They have no intention of releasing the code or creating a commercial product out of the modified glasses.
Technical Breakdown
The modified Ray-Ban glasses achieve facial recognition through a combination of techniques:
- Reverse Facial Recognition: Matching faces captured by the glasses with publicly available images online.
- PimEyes: A search engine specializing in facial recognition.
- Large Language Models (LLMs): AI systems used to analyze online information about the identified person.
- FastPeopleSearch: A website providing additional personal information.
Meta’s Response
Meta, the company behind the Ray-Ban smart glasses, acknowledges that facial recognition technology like PimEyes can be used with any camera, but it is not specific to their product. However, the casual design of the Ray-Ban glasses allows for discreet image capture, potentially without knowing the person being photographed.
The Future of Facial Recognition Glasses
The students’ project highlights the potential for future smart glasses equipped with more powerful processors, on-device AI, and augmented reality to pose even greater privacy risks.
Pimeye’s Response
The developers of PimEyes expressed surprise at the students’ project, claiming their search engine is not designed to identify individuals.
Microsoft Confirms Exploited Zero-Day In Windows Management Console
Microsoft issued an urgent warning about an actively exploited code execution vulnerability in a Windows component used for system configuration and monitoring.
The zero-day, tagged as CVE-2024-43572, is a remote code execution issue in Microsoft Management Console (MMC). Attackers are using malicious Microsoft Saved Console (MSC) files to execute remote code on targeted Windows systems. This vulnerability has a CVSS severity score of 7.8/10 and is part of a Patch Tuesday rollout to cover at least 119 documented vulnerabilities.
Microsoft also flagged CVE-2024-43573 for urgent attention, warning that a flaw in the Windows MSHTML platform is in the “exploitation detected” category. Additionally, Adobe released urgent patches to fix security defects in multiple product lines and warned of code execution risks on Windows and macOS platforms.
American Water Shuts Down Customer Portal Amid Cyber Security Incident
The American Water Company, the largest regulated water and wastewater utility company in the United States, recently experienced a cybersecurity incident, prompting the company to take its customer portal offline. The incident, which involved unauthorised activity on its computer networks, led the company to activate its incident response protocols and disconnect certain systems. While billing has been paused and late fees waived during this time, the company assured that its water and wastewater facilities remain unaffected, and the water is safe to drink.
In response to the incident, the company has engaged third-party security experts and law enforcement to contain, mitigate, and investigate the nature of the incident. Although the company did not confirm whether customer or employee data was compromised, it emphasised its commitment to strengthening cybersecurity and prioritizing the security of its systems and customer data.
This incident comes at a time when government agencies are increasingly concerned about cyberattacks on water and wastewater facilities, particularly by foreign nation-state actors. In light of recent attacks and potential vulnerabilities, efforts are underway to enhance water system security across the nation, including the establishment of a Water Sector Cybersecurity Task Force by the Environmental Protection Agency (EPA) to address cybersecurity challenges and reduce the risk of cyberattacks on water systems nationwide.
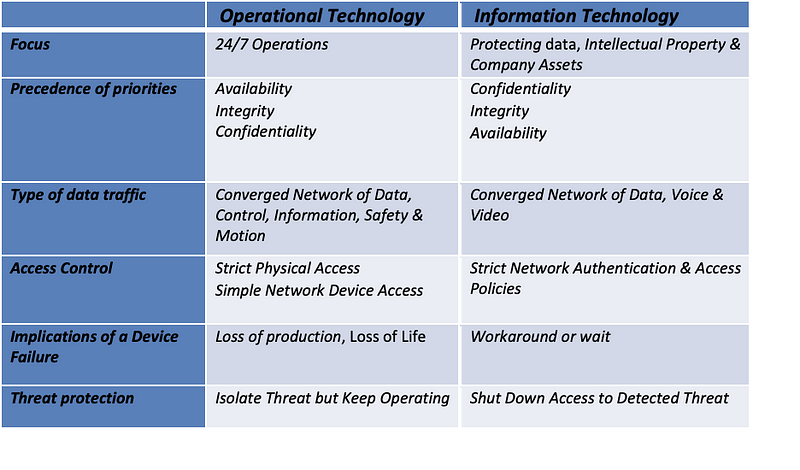
Given the persistent threats to critical infrastructure utilities, including water facilities, there is a growing emphasis on improving operational technology (OT) and industrial control systems (ICS) security. Collaborative efforts involving various countries and cybersecurity agencies are aimed at promoting best practices and enhancing the security of critical infrastructure organisations.