Your Weekly Cybersecurity Update (2 August 2024)
- SBOMs: A Crucial Tool Hampered by Standardization Issues
- Mysterious Rings and QR Codes: The Emergence of Brushing Scams
- France Battles Cyberespionage Ahead of the Olympics
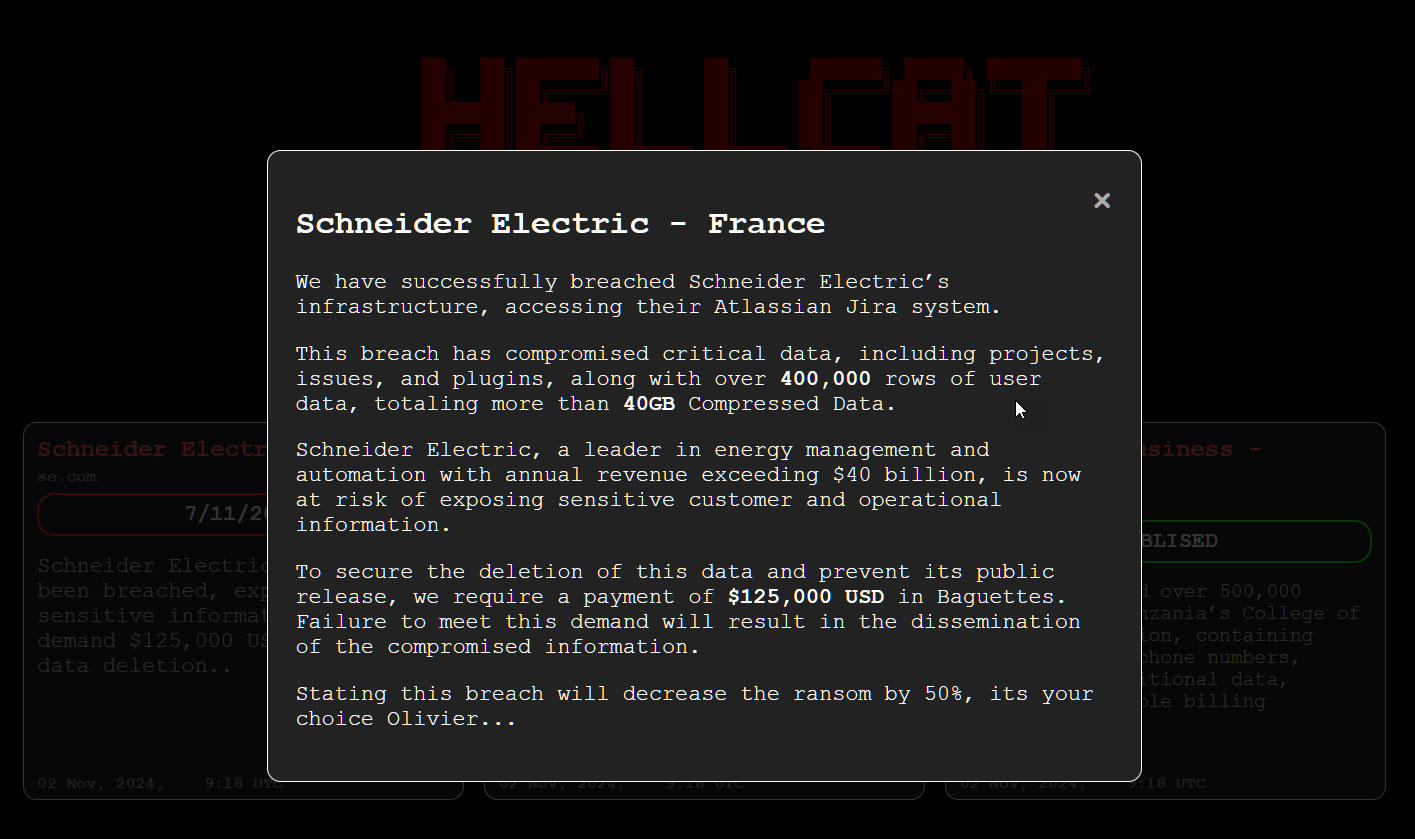
- GitHub’s Dark Secret: Deleted Data Never Really Dies
- Sitting Ducks: DNS attacks enable hackers to take control of more than 35,000 domains
- U.S. Trades 5 Cybercriminals to Russia in Prisoner Swap
SBOMs: A Crucial Tool Hampered by Standardization Issues
Software Bills of Materials (SBOMs) have become essential for securing software supply chains in the wake of high-profile cyberattacks. Mandated by government agencies and increasingly adopted by enterprises, SBOMs promise transparency into software components and their vulnerabilities.
However, the potential of SBOMs is being undermined by a lack of standardization. Competing formats and varying implementation methods have created confusion and inefficiency for organizations. This has turned what should be a straightforward tool for identifying and addressing vulnerabilities into a complex and costly process.
Experts are calling for a unified SBOM standard to streamline the process and maximize the benefits of this critical technology. Achieving this will require collaboration between industry leaders, standards bodies, and government agencies.
By creating a single, standardized SBOM format, the tech industry can significantly improve software supply chain security and protect against future cyberattacks.
Mysterious Rings and QR Codes: The Emergence of Brushing Scams
A complex new cyber scam has surfaced, involving the delivery of unsolicited diamond rings and suspicious QR codes to unsuspecting victims. The scam, believed to be a form of “brushing,” has ensnared at least one Australian woman.
In a typical brushing scam, scammers send unsolicited items to victims to boost fake online reviews for their products. However, this latest iteration includes an added layer of mystery and potential danger. Victims are receiving diamond rings (fake ones of course!) accompanied by QR codes, which experts warn could be used for phishing attempts.
Cybersecurity experts are urging caution as the scam demonstrates the increasing sophistication of online criminals. By creating convincing fake websites and exploiting social media platforms, scammers are able to target a wide range of victims.
To protect yourself from falling victim to this or similar scams, it’s essential to be vigilant when making online purchases. Be wary of deals that seem too good to be true, avoid clicking on suspicious links or pop-up messages, and carefully research any unfamiliar websites.
If you receive an unsolicited package, do not scan any QR codes or open any links included within it. Instead, report the incident to local authorities and your bank.
Australians lost a staggering $74 million to online scams last year, highlighting the growing threat posed by cybercriminals.
France Battles Cyberespionage Ahead of Olympics
French authorities have launched a massive operation to combat a cyberespionage campaign targeting thousands of computers within the country. The initiative comes just as the Paris Olympics are set to begin, highlighting the heightened security concerns surrounding the global event.
The malware used in the attack, PlugX, is a well-known tool employed by Chinese state-sponsored hacking groups. The operation aims to remove the malicious software from infected devices and disrupt the broader botnet.
While there’s no direct confirmation that the cyberattack is Olympics-related, the timing underscores the increased vulnerability of large-scale events to cyber threats. French officials have acknowledged the inevitability of cyberattacks during the Games but vowed to minimize their impact.
The country is also bracing for other security challenges, including potential terrorist attacks and sabotage, as evidenced by recent disruptions to the national railway system.
The operation to clean up infected systems is a significant step in France’s efforts to protect its digital infrastructure and safeguard sensitive information.
GitHub’s Dark Secret: Deleted Data Never Really Dies
A new security vulnerability has been uncovered on GitHub that allows access to data from deleted repositories and forks. This means that sensitive information, such as API keys, can persist even after being supposedly erased.
Security researchers at Truffle Security have dubbed this issue a “Cross Fork Object Reference” (CFOR). They demonstrated how deleted code, including private data, can still be accessed through forks of the original repository. This raises serious concerns about data privacy and security.
While GitHub maintains that this is expected behaviour, critics argue that it undermines user trust and expectations about data deletion. The platform’s response has been to classify this as a “feature” rather than a vulnerability.
This discovery highlights the potential risks associated with relying solely on code-hosting platforms for data security. Organizations need to be aware of these limitations and implement additional safeguards to protect sensitive information.
As the digital landscape evolves, it’s increasingly clear that data deletion is a complex issue with far-reaching implications for individuals and businesses alike.
Sitting Ducks: DNS attacks enable hackers to take control of more than 35,000 domains
The “Sitting Ducks” attacks, which allow cybercriminals to claim domains without proper access, pose a significant threat. Multiple threat actors have used this method to carry out various malicious activities, compromising the security and integrity of online platforms.
Domain owners must regularly review their DNS configurations, especially on older domains, and update the delegation records with active DNS services. Registrars should also conduct proactive checks for weaknesses and ensure the establishment of a secure DNS service before delegating name servers.
Moreover, regulators and standards bodies need to develop long-term strategies to address DNS vulnerabilities. It is essential to press DNS providers to take more action to mitigate Sitting Ducks attacks and strengthen overall security measures to safeguard the online environment.
U.S. Trades 5 Cybercriminals to Russia in Prisoner Swapthe
Twenty-four prisoners were released in a prisoner swap between Russia and Western countries. Eight Russians, among them five convicted cybercriminals, were exchanged. Russia, in return, has released 16 prisoners, including Wall Street Journal reporter Evan Gershkovich and ex-U.S. Marine Paul Whelan.
One of the notable Russian hackers released in the swap is Roman Seleznev, 40, who was sentenced in 2017 to 27 years in prison for racketeering convictions related to theft and sale of payment card data. Seleznev, also known by hacker handles “Track2,” “Bulba,” and “nCux,” is the son of Valery Seleznev, a prominent member of the Russian parliament considered an ally of Vladimir Putin. US prosecutors demonstrated that Seleznev managed to evade the law for years by leveraging contacts at the Russian FSB and changing hacker handles periodically.