Cybersecurity Challenges Of The “Interconnected World”
Originally published at https://cyberbakery.net on February 19, 2022.

Originally published at https://cyberbakery.net on February 19, 2022.
The Interconnected World of billions of IoT (Internet of Thing) devices has revolutionised digitalisation, creating enormous opportunities for humanity. In this post, I will be focussing on the uniqueness of the security challenges presented by these connected IoT devices and how we can respond.
We are ever more connected in the history of humanity. Every time we wear or connect a device to the Internet, we extend this connectivity, increasing your ability to solve problems and be more efficient and productive. This connected world of billions of IoT (Internet of Thing) devices has revolutionised digitalisation. However, such massive use of connected devices has presented a different cybersecurity challenge. A challenge that compelled c-suite to develop and implement separate cybersecurity programs to respond to two competing security objectives. Where IT (information Technology) focuses on managing confidentiality and integrity more than the system’s availability, OT(Operational Technology) focuses on the availability and integrity of the industrial control system. The convergence of the two desperate technology environments does improve efficiency and performance, but it also increases the threat surface.
What makes OT different from IT?
IT predominantly deals with data as a product that requires protection. On the other hand, data is a means to run and control a physical machine or a process. The convergence of the two environments has revolutionised our critical infrastructure, where free exchange data has increased efficiency and productivity. You require less physical presence at the remote sites for initiating manual changes. You can now remotely make changes and control machines. With Industry 4.0, we are witnessing the next wave of the industrial revolution. We are introducing a real-time interaction between the machines in a factory (OT) and the external third parties such as suppliers, customers, logistics, etc. Real-time exchange of information from the OT environment is required for safety and process effectiveness.
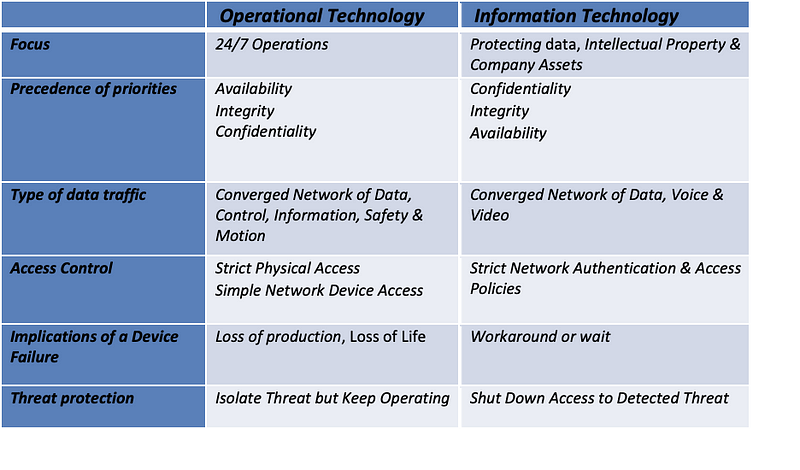
Unfortunately, the convergence of IT into OT environments has exposed the OT ecosystem to more risks than ever before by extending the attack surface from IT. The primary security objective in IT is to protect the confidentiality and integrity of the data ensuring the data is available as and when required. However, in OT safety of the people and the integrity of the industrial process is of utmost importance.
The following diagrams show a typical industrial process and the underlying devices in an OT environment.
As you can see, the underlying technology components are very similar to IT and, therefore, can adopt the IT security principles within the OT environments. OT environments are made of programmable logic controllers (PLCs) and computing devices such as Windows and Linux computers. Deployment of such devices exposes the OT environment to similar threats in the IT world. Therefore, the organisations need to appreciate the subtle similarities and differences of the two environments applying cybersecurity principles to improve the security and safety of the two converged environments.
Risk profile of the converged environment
The interconnected OT and IT environments give an extended attack surface where the threats can move laterally between the two environments. However, it was not until 2010 the industry realised the threats, thanks to the appearance of the Stuxnet. Stuxnet was the first attack on the operational systems where 1000 centrifuges were destroyed in an Iranian nuclear plant to reduce their uranium enrichment capabilities. This incident was a trigger to bring cybersecurity threats to the forefront.
Following are some of the key threats and risks inherent in a poorly managed converged environment.
* Ransomware, extorsion and other financial attacks
* Targeted and persistent attacks by nation-states
* Unauthorised changes to the control system may result in harm, including loss of life.
* Disruption of services due to the delayed or flawed information relayed through to the OT environment leads to malfunctioning of the controls systems.
* Use of legacy devices incapable of implementing contemporary security controls be used to launch a cyberattack.
* Unauthorised Interference with communication systems directs operators to take inappropriate actions, leaving unintended consequences.
Cybersecurity Behaviours and Practices
As noted earlier in this post, the converged IT & OT environments can take inspiration from IT security to adopt tools, techniques and procedures to reduce cyberattack opportunities. Following are some strategies to help organisations set up a cybersecurity program for an interconnected environment.
Reduce complexity and attack opportunities
* Reduce the complexity of networks, applications, and operating systems to reduce the “attack surface” available to an attacker.
Better perimeter and service knowledge
* Map the interdependencies between networks, applications, and operating systems.
* Identify assets that are dealing with sensitive data.
Strengthen internal collaboration
* Avoid conflicts between business units (business owners, information technology, security departments, etc.) and improve internal communication and collaboration.
Strengthen External collaboration
* Improve and strengthen collaboration with external entities such as government agencies, Vendors, customers etc., sharing threat intelligence to improve incident response.
Know your insider threats
* Identify and assess insider threats.
* Regularly monitor such threats, including your employees, for their changing social behaviours.
Increase awareness and training
* Invest in targeted employee security awareness and training to improve behaviours and attitudes towards security.
Strengthen Integration by data/traffic analysis
* Improve network traffic data collection and analysis processes to improve security intelligence, improving informed and targeted incident response.
Build in-house security capabilities
* Build in-house security competencies, including skilled resources for continuity and enhanced incident response.
Limit BYOD (bring your device)
* Clear BYOD policy must be defined and implemented within the IT & OT environments.
* Only approved devices can always be connected to the environment with strict authorisation and authentication controls in place.
* Monitor all user activity whilst connected with the network
Align Cyber Program with Industry standards
* Align your cybersecurity program with well-established security standards to structure the program.
* Some of the industry standards include ISO 27001–27002, RFC 6272, IEC 61850/62351, ISA-95, ISA-99, ISO/IEC 15408, ITIL, COBIT etc.
Implement principles-based context-aware security architecture
* Ensure clear demarcation of the IT & OT environments. Limit the attack surface.
* Virtual segmentation with zero trust. Complete isolation of control and automation environments from the supervisory layer.
* Implement tools and techniques to facilitate incident detection and response.
* Implement a zero trust model for endpoints
Implement threat hunting
* Implement threat hunting capabilities for the converged environment focused on early detection and response.
Conclusion
The last fifteen years or so have shown us how vulnerable our technology environments are. Protection of these environments requires a multi-pronged and integrated strategy. This strategy should not only consider external risks but also consider insider threats. A prioritised approach to mitigate these risks requires a holistic approach that includes people processes and technology. Benchmarking exercises could also help organisations to identify the “state of play” of similar-sized entities. We are surely seeing consistent investment in the security efforts across the board, but we still have to work hard to respond to ever-changing threat scenarios continuously.
Please enable JavaScript to view the




